A recent survey by Specops found the most common security breaches in healthcare are Man in the Middle (MITM) attacks

Healthcare data and patient records are especially sensitive in comparison to other personal information, making them more valuable to cyber criminals (Credit: Jefferson Santos/Unsplash)
Swedish tech company Specops Software recently revealed that Man in the Middle (MITM) cyber-attacks are the most prevalent threat faced by healthcare companies.
After surveying more than 1,700 individuals across several industries, Specops found that 62% of respondents within the medical sector had been a victim of an MITM attack in the past five years.
We take a closer look at MITM attacks, and what healthcare businesses can do to guard against them in the future.
What are Man in the Middle cyber-attacks?
Man in the Middle attacks allow hackers to place themselves between two communicating parties, and intercept, send and receive data never meant for them.
A key detail in MITM attacks is that the victim and the person they are attempting to communicate with do not realise the “man in the middle” is there — until it is too late.
The traditional approach involves a hacker being in physical proximity to their victim, and gaining access to an unsecured, or at least poorly secured, WiFi router.
These circumstances are often found in public areas with free WiFi hotspots, but can also occur in homes if they do not have a well-protected network.
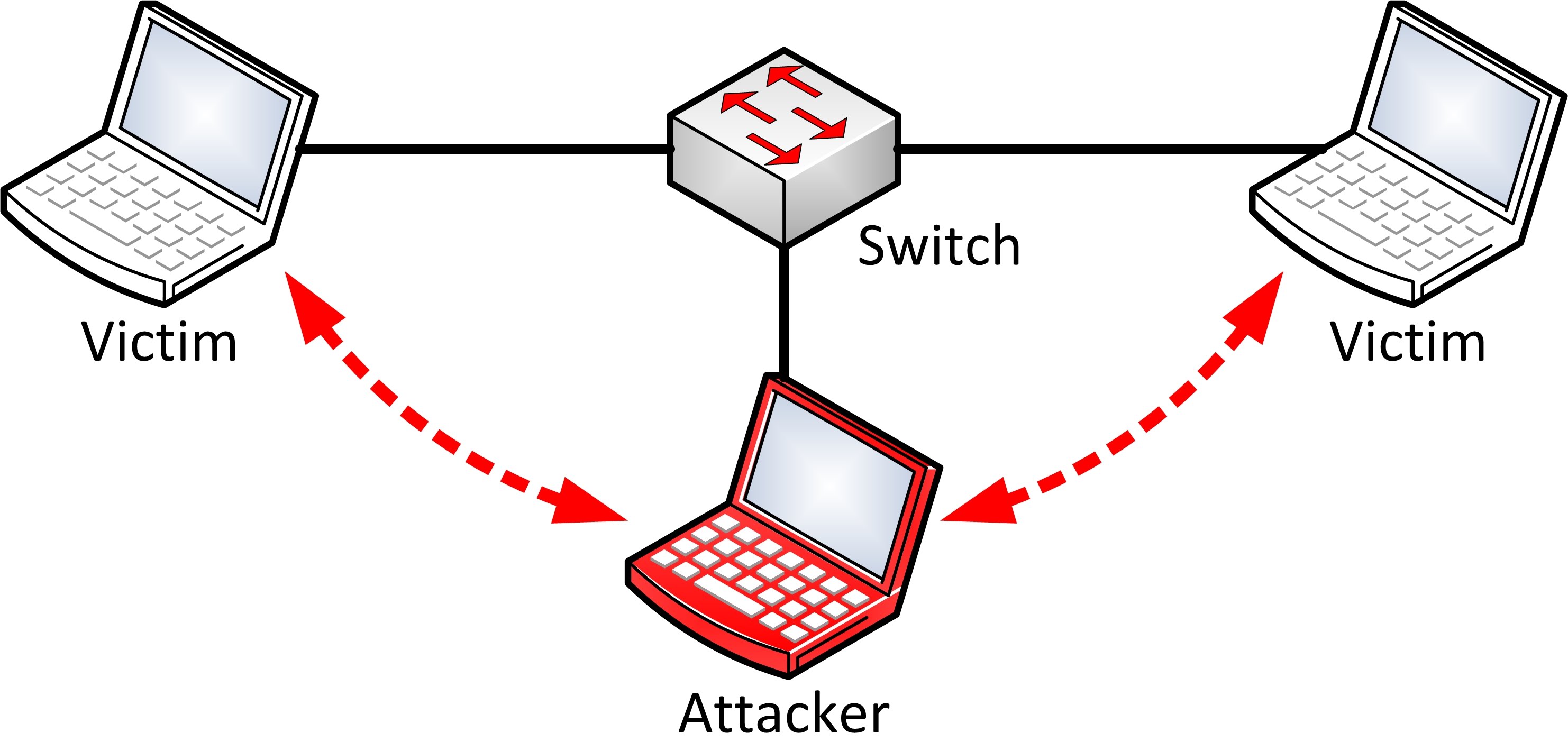
Attackers can scan the routers and look for specific vulnerabilities — such as a weak password — before deploying tools to intercept and read the data of anyone using the network.
They can also place themselves between the user’s computer and the websites they visit, obtaining a range of personal information including login credentials and banking details.
The hacker must unencrypt the victim’s data to be able to read it and use it maliciously.
Aside from this more traditional MITM security breach, there are also Man in the Browser (MITB) attacks — which involve the use of malware (malicious software).
How do Man in the Browser attacks differ from MITM?
Malware can be entered into a victim’s computer in several ways.
One method typically used by hackers is phishing, which involves sending an email or text message that appears to be from a trusted sender, but is disguised malware designed to trick to victim into handing over sensitive information.
On its website, US cyber security company Norton uses the following example to demonstrate this: “Let’s say you received an email that appeared to be from your bank, asking you to log in to your account to confirm your contact information.
“You click on a link in the email and are taken to what appears to be your bank’s website, where you log in and perform the requested task.
“In such a scenario, the man in the middle sent you the email, making it appear to be legitimate.
“They also created a website that looks just like your bank’s website so you wouldn’t hesitate to enter your login credentials after clicking the link in the email.”
The point at which the victim clicks on the link is when malware is loaded onto their device, allowing the hacker to record and steal data sent between the victim and the fake website.
This means that once the victim enters their login credentials for their bank online, they are sent straight to the man in the middle.
The threat to healthcare companies
In MITM attacks on healthcare systems, hackers place themselves between communicating parties — either two healthcare providers, or a patient and their provider.
This can also be done by intercepting communications between medical devices in the same hospital or care facility, meaning the ever-increasing use of AI-based technologies, particularly in the cloud, exposes the industry to more cyber-attacks.
Once a cyber-attacker has done this, they can obtain, and copy or alter patient data — such as test results. Patient data is especially sensitive in comparison to other personal data, making it more valuable to cyber criminals.

Hackers can also introduce malware into patient records, and threaten to maliciously publish them online or deny access to them until a sum of money is paid. This is commonly referred to as a ransomware attack.
Cyber security providers often use hypertext transfer protocol secure (HTTPS) products to intercept communications and inspect network traffic for malware.
But in 2017, the US Department of Health and Human Services (HHS) warned that HTTPS protocols could make network connections less secure, and more vulnerable to MITM attacks.
The increasing use of smartphone apps in giving patients improved access to their healthcare information has also led to a need for stricter mobile device cyber security.
What can healthcare companies do to prevent MITM attacks?
As part of its December 2019 report on the most common hacking methods, Specops’ cyber security expert Darren James provided the following tips on how to combat future attacks:
1. Always update
This includes antivirus software. Programmes are constantly updated, and every update provides vital patches and bug fixes. Missing any of these could expose a weakness to potential hackers.
2. Nip it in the bud
At the first sign of strange activity e.g. unusually large data usage, slow service, or pop-ups, flag it. A superior will be able to carry out necessary checks and prevent a potential virus from worsening.
3. Don’t believe everything you read
Many still fall for easy phishing scams and clickbait viruses, resulting in serious security breaches. Always question what is presented to you.
4. If in doubt, refrain from clicking
It’s better to be safe than sorry. There’s no way to know the contents of a document or link before opening, especially as hackers adapt to the improving technological space. Ask for advice, but ultimately avoid it if you are unsure.
