Protecting healthcare IT is likened to children in a sandpit - they'll behave when you're watching them but turn your back and they'll start misbehaving

The IoMT is now a major part of running hospitals with so many medical devices connected (Credit: PxFuel)
With the internet of medical things (IoMT) a growing influence in clinical settings, hospitals and other institutions must increasingly adopt cyber security defences. Bob Zemke, director of healthcare solutions at San Jose networking company Extreme Networks, outlines the more important considerations.
Reimagining healthcare by reducing costs and improving patient outcomes has been a subject of debate for decades – and IoT healthcare solutions have proved a popular choice.
So much so that 20 to 30 billion connected IoT and medical devices are expected to be a part of the healthcare ecosystem by the end of 2020, according to Frost & Sullivan’s Internet of Medical Things, Forecast to 2021 report.
The acceleration of the IoMT over recent years has brought huge benefits to medical organisations and their patients alike.
From giving patients greater control over their treatment to alleviating some of the cost, access, and care co-ordination challenges currently facing the healthcare industry, IoMT is poised to transform how we keep people healthy.
Why cyber security is an increasing part of the IoMT
Yet, despite its benefits, IoMT has offered an easy gateway for cyber criminals seeking to exploit and capitalise on vulnerabilities.
The Open Source Cybersecurity Intelligence Network and Resource reported there are on average 6.2 vulnerabilities per medical device.
When considering the vast volume of medical devices now present within hospitals and clinical settings, this paints a worrying – although perhaps not unexpected – picture.
As an analogy, children in a sandpit behave (most of the time) when you are watching them, but turn your back and they can soon start misbehaving. The same goes for IoMT.
If devices aren’t monitored, observed and updated – on a regular basis – vulnerabilities can inevitably be introduced which go undetected.
In fact, our recent global survey found that one in five healthcare IT professionals were unsure if every medical device on their network had all the latest software patches installed, meaning they effectively had a porous security infrastructure that could easily be bypassed.

A security breach in any setting poses a huge challenge, but in healthcare, it can be a matter of life and death.
So what are the three things healthcare institutions can do to reap the benefits from IoMT devices and avoid them behaving like “children in a sandbox” – being vulnerable to attack?
How to set up cyber security for IoMT
1) Enforce a cloud-driven network to accommodate all IoMT devices
To accommodate all IoMT devices effectively, healthcare organisations should consider transitioning to a cloud-driven network.
The latest cloud solutions promise to radically transform how businesses manage their networks, enabling a shift beyond basic network management and into the realms of real-time innovation and insight.
More importantly, they offer increased availability, flexibility, and reduced operational complexity to support ever-increasing connectivity demands.
Not only does this help to alleviate pressure from IT, enabling them to focus on strategic, mission-critical initiatives, but it can also save costs.
According to our own research, 88% of healthcare organisations to date have reduced the cost of software using the cloud.
The rate of cloud adoption in healthcare has been steadily increasing.
Cloud networks have been tried and tested, IT departments increasingly value the agility and flexibility they offer, and major advancements in next-generation cloud infrastructure are underway.
For forward-looking healthcare facilities, a cloud-driven network offers a smart way to radically simplify, secure and future-proof the organisation.
2) Gain visibility of all devices – physically and on the network
A NursingTimes.net survey, polling 1,000 nurses, discovered that at least one in three nurses spent an hour or more per shift searching for medical equipment to use with their patients.
That’s equivalent to about 6,000 hours a month. With the healthcare industry being time-critical, every minute counts.
To free up vital nursing time and safeguard against security issues, it is essential that hospitals have visibility of all their devices, both physically and on the network.
To achieve this, healthcare institutions should look to “eyeballs on the edge” to help them easily keep track of equipment – such as mobile X-ray machines, ultrasounds or infusion pumps – as it moves around a building.
Eyeballs on the edge does not refer to physical security, but the use of video analytics in combination with edge computing.
The name is derived from how this technology can perform relatively simple image recognition tasks by using a video stream source.
In other words, tasks that could be performed by the human eye.
Instead of different wireless and ultra-wideband technologies, eyeballs at the edge offers the most promise when keeping track of IoMT devices.
Thanks to simple video analytics, it can be trained to identify medical devices and track them as they are transported around hospitals just as a human would.
This not only empowers staff to focus on the delivery of clinical care and saves considerable time, but optimises device security.
3) Secure all devices on the network
Security came into stark focus for the healthcare industry following notable malware attacks, such as WannaCry in 2017.
This wake-up call couldn’t have come soon enough considering the breadth of sensitive data stored on hospital servers and the volume of life-saving devices which can be compromised by a security breach.
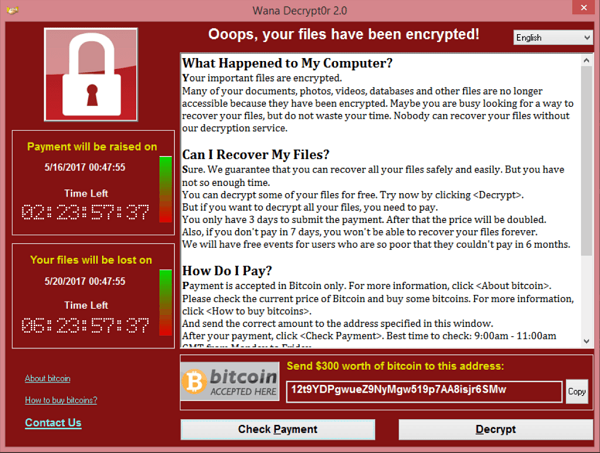
But the risk is yet to slow down. In fact, healthcare became the leading vertical to report data breaches during the first half of 2019, according to the Cyber Security Hub.
A network is only as resilient as its weakest link.
This means it’s more critical than ever for healthcare organisations – of whichever size and type – to secure all devices across all network endpoints, from CCTV cameras to ageing wired devices around a room, a building or even a campus.
That means deploying a solution that can monitor all traffic to and from IoMT devices and restrict who and what each device can communicate with.
Taking steps to secure and monitor what machines and devices are doing behind our backs – just like children in a sandpit – is critical.
And a robust, resilient – possibly cloud-driven – network infrastructure is central in doing so.
As healthcare organisations look to reap the benefits from IoMT devices and avoid becoming easy pickings for cyber criminals, getting the right infrastructure and processes in place to protect their frontline will help pave the way to greater efficiency and better patient outcomes.
